CAN transceiver provides cyber security without encryption
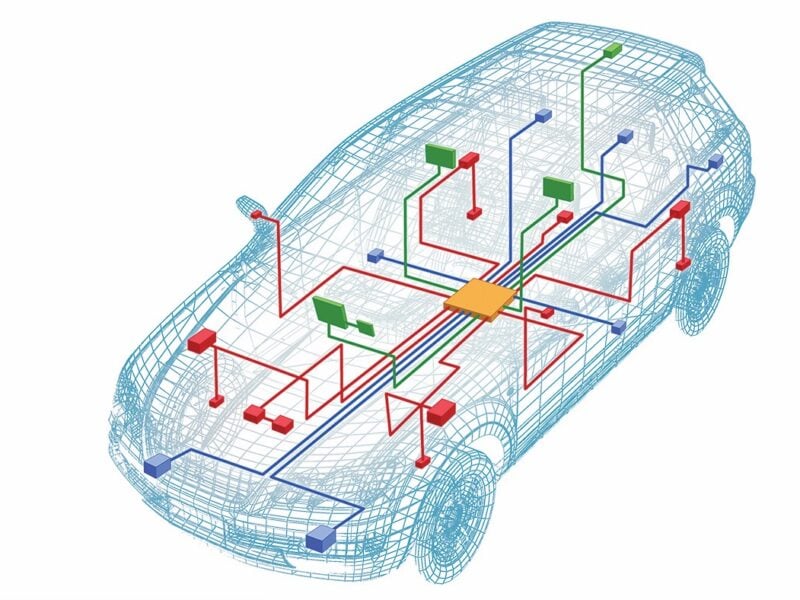
CAN networks connect (almost) all electronic control units (ECUs) with each other. Despite their inherent lack of data security and hence their vulnerability to cyber attacks, insiders agree that there is no cost-effective alternative in sight and therefore CAN networks are likely to remain the most important network for the coming decade. As the proportion of electronics in vehicles continues to grow, the amount of real-time data exchanged in CAN networks is also increasing.
However, because CAN is a multi-point connection network and most of the data communication within the vehicle has so far been unsecured, a single compromised ECU can access the connected ECUs directly. The solutions available today traditionally protect CAN communication using a Message Authentication Code (MAC) based on cryptography and complex key management. However, this requires increased CAN bus utilization and message latency and requires significantly more computing power.
Existing ECUs cannot simply be upgraded to support secure CAN messages if the processors do not have sufficient computing power. With secure CAN transceivers, however, car manufacturers can secure the messages of already installed ECUs, which makes it easier and quicker to implement safety measures than replacing the existing ECUs with safe ones.
See also: “Vatican” stops hacker attacks on cars
NXP has developed a purely transceiver-based solution for the CAN network that provides security – with no additional bandwidth requirements, no delays and no additional processor load, the chipmaker promises. This approach adds an additional layer to crypto-based security solutions, either in a defense-in-depth (DiD) concept or as a standalone option.
Security features of the CAN transceiver
Spoofing protection on the transmit side: Protects the CAN bus from a compromised ECU by filtering messages in the send path based on CAN message IDs. If the ECU tries to send a message with an ID that was not originally assigned to it, the safe CAN transceiver can prevent transmission to the bus.
Spoofing protection on the receiving side: Complementary protection is used to void messages on the bus using a CAN message ID assigned during transmission. Thanks to this method, each ECU has the ability to protect its own IDs – in case a compromised ECU manages to send a message with the same ID.
See also: Karamba heals CAN bus’ innate lack of security
Tamper protection: By making messages on the CAN bus invalid, manipulations can be prevented and the process is a clear signal that a compromised control unit is involved in the transmission.
No bus overload thanks to control of transmission processes: A permanent limitation of the number of messages sent per ECU from the transmitter side helps to prevent the bus from being overloaded and ensures that it remains free for certain critical tasks.
Further reading:
Opinion: CAN fault confinement: It is a feature, not a flaw!
 If you enjoyed this article, you will like the following ones: don't miss them by subscribing to :
eeNews on Google News
If you enjoyed this article, you will like the following ones: don't miss them by subscribing to :
eeNews on Google News